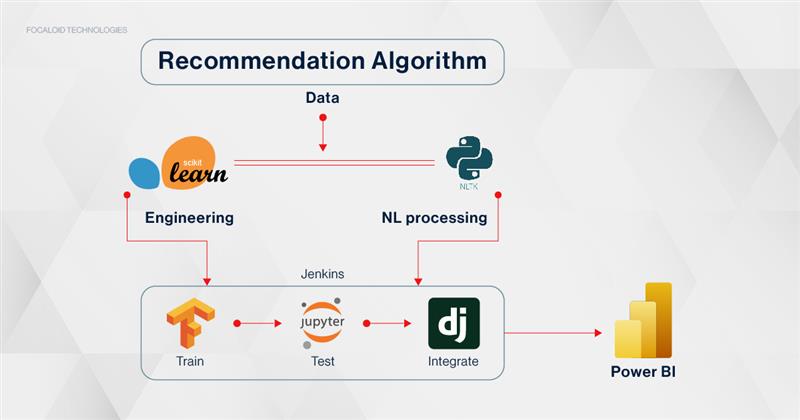
BLOCKCHAIN |
BUSINESS |
IOT |
How to protect your business from Cybercrime in 2019
28/09/2021
20mins
Anish Prakash
BUSINESS,BLOCKCHAIN,IOT
Technology is rapidly changing businesses. Today, the focus is no longer on adopting automation practices. Instead, it is on how to improve on automated systems as technology advances. As companies invest in improving their cybersecurity systems and processes, they also need to be aware that there could be inherent vulnerabilities they're yet to discover that cybercriminals could be working on. This makes it absolutely essential for businesses to be more innovative in their cybersecurity strategies. According to Gemalto (an international digital security company), there were over 3.2 billion data records that were compromised in just the first half of 2018. Some of the most common cybercrimes are ransomware, targeted phishing attacks, denial-of-service (DOS) attacks, and advanced persistent threats.
Such cyber attacks can result in major financial meltdowns for companies that are not well prepared. In most cases, this would be small- and medium-sized businesses. Without adequate cybersecurity measures, businesses are at high risk and owners need to urgently become more security conscious before they suffer unforetold losses that would result in the company's downfall. Following these five actions would be a good start towards establishing a security-conscious business:
1.Backup system implementation
A couple of years ago, backup systems involved costly in-house hardware and off-site location storage. As technology advanced, backup systems became less costly when a wide range of cloud technology solutions became available. Reliable and safe, this technology would help to restore your system data – either the entire system or parts of the system. Business owners should invest in enterprise-level cloud storage systems if they're not already utilizing in-house hardware and off-site location storage. Ease of access to this technology for system restoration significantly reduces downtime.
2.Vulnerability scan
Businesses are keeping up with technology by implementing access cards, allowing employees to access systems with mobile devices, installing cameras in and around the workplace, and increasing access to the internet. All these areas need to be examined as potential entry points for cyber attacks, in addition to employee workstation and communication systems.
3. System threats assessment
Assessments to system threats include both customers and vendors, and anyone who has access to the company systems. Particular attention should be placed on data logs, emails, client lists, backups, emails, and passwords.
4. Preventative systems implementation and maintenance
This is important for the protection of the company’s assets and should be done by an external party who would be better equipped to assess your company. If preventative systems are not in place, hackers can easily access the company’s system and steal data that can cripple the company. Ensure that the preventative system includes both physical and digital security, and that it is robust enough to defend against intruders. Maintenance of this system is also very crucial and should not be neglected.
5.Security audit
A security audit should be conducted to help discover system vulnerabilities, where they exist, how it can be secured and how to resolve existing vulnerabilities. Most insurance companies require that security audits be performed and would have third-party contractors who would be do it for them.
Cyberattacks and cybercrime should not be taken lightly. Policies and state regulations need to be constantly being revised and put in place to guard against it. As a business owner, you too must play your part because your business is your livelihood and the livelihood of your employees and their families.
Published:
Share: